OVERVIEW:
OSI(Open System Interconnection) model is a conceptual model created to communicate over the network. Although the modern Internet is not based truly on the OSI model but on a simpler TCP/IP model.
HISTORY:
OSI model was introduced in 1983 by major computer and telecom companies. Later adopted by ISO(International Organisation for Standardization) as an international standard in 1984.
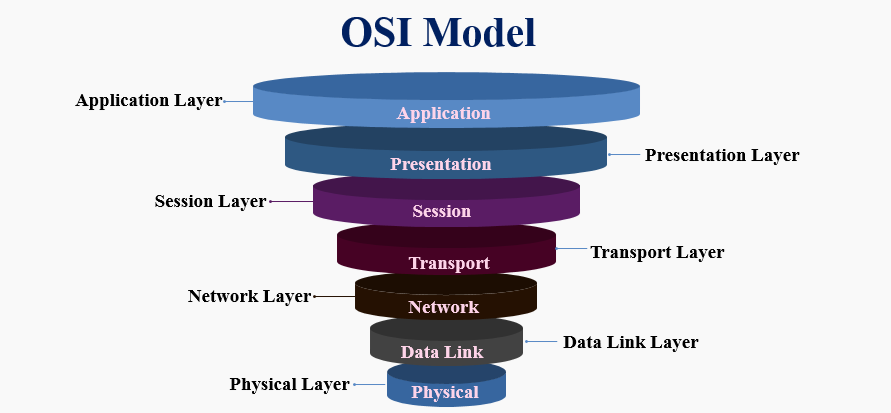
LAYERS OF OSI MODEL:
OSI model consists of 7 layers :
Application Layer
Presentation Layer
Session Layer
Transport Layer
Network Layer
Data Link Layer
Physical Layer
1. APPLICATION LAYER:
It is present at the top of the OSI model used by network applications like Chrome, Firefox, G-mail etc. An application layer is not an application, but it performs the application layer functions.
FUNCTION:
- FILE TRANSFER, ACCESS AND MANAGEMENT: An application layer allows users to access the files in a remote computer, to retrieve files from a computer.
PROTOCOLS USED:
A few application layer protocols are HTTP (Hypertext Transfer Protocol) for web surfing, FTP (File Transfer Protocol) for file transferring, SMTP (Simple Mail Transfer Protocol) for mail sending and receiving, DNS (Domain Name System) for converting domain names like www.google.com to its IP 197.193.232.3. etc.
2. PRESENTATION LAYER:
It receives data from the application layer. This layer serves as a data translator for the network. Data received is manipulated here.
FUNCTIONS:
TRANSLATION: In this process, the data gets converted into a simple binary form.
DATA COMPRESSION: It can be lossy or lossless. In lossy, the significant piece of data is removed to reduce size. While in lossless the data is transformed through encoding and then its size gets reduced.
ENCRYPTION/DECRYPTION: Here the data is encrypted by the sender's side and decrypted by the receiver's side. As the data may often be sensitive, scrambling the data and then putting back together is Encryption and decryption.
PROTOCOLS USED:
A few presentation layer protocols are AFP (Apple Filing Protocol) is a network control protocol that offers services to macOS, NCP (NetWare Core Protocol) is used to access files, print, clock synchronization, messaging etc., SSL (Secure Socket Layer) is used to provide security to data that is being transferred between the web browser and the server.
3. SESSION LAYER:
These layers help in establishing sessions between different machines. It helps in maintaining, and terminating sessions between end-user applications.
FUNCTIONS:
AUTHENTICATION: To establish a connection within the server. To know whether the other end-user is a legitimate one.
AUTHORISATION: In this, although authentication of the user is done but you cannot access the files or data to which you are not authenticated.
SESSION MANAGEMENT: The session layer helps in managing a session which includes opening, closing and managing sessions.
PROTOCOLS USED:
A few Session layer protocols are ADSP (Apple-Talk Data Stream Protocol) which allows to LAN to be connected with no setup, RTCP (Real-Time Transport Control Protocol) which provides feedback on the Quality of service, PAP (Password Authentication Protocol) which is used by PPTP (Point to Point Tunnelling Protocol) to validate users, etc.
NOTE:
ALL THE ABOVE 3 LAYER'S FUNCTIONS ARE PERFORMED BY THE BROWSER ITSELF.
4. TRANSPORT LAYER:
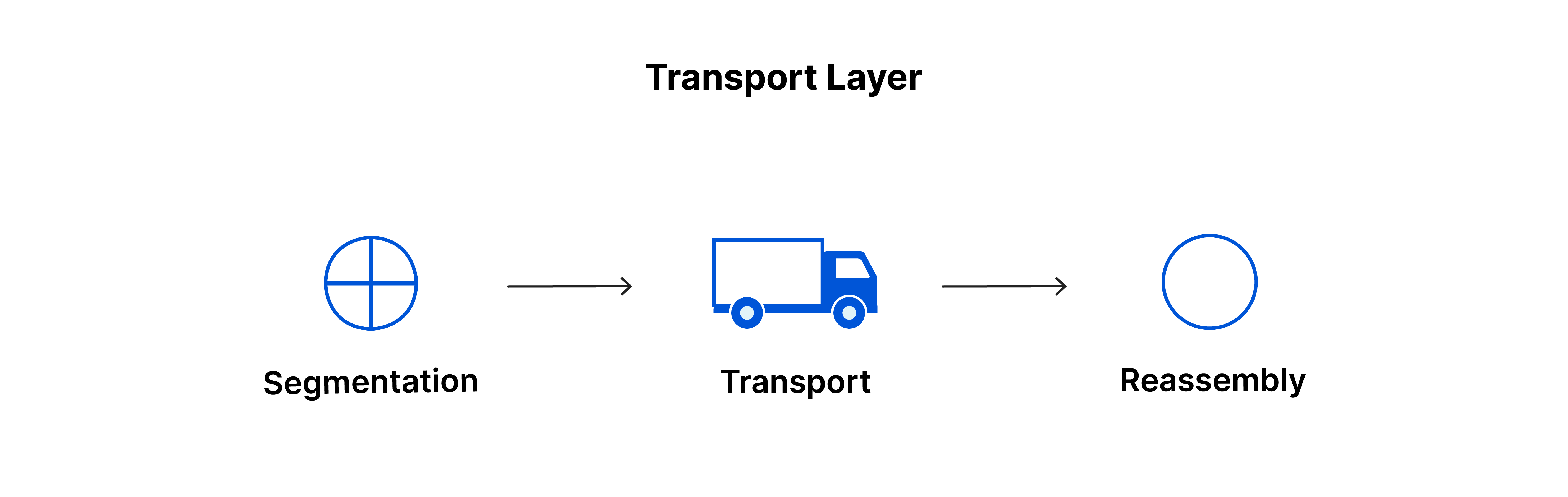
This layer takes data from the session layer and breaks it into segments on the sender's end. On the receiver's end, it reassembles the segments. It also checks how much data is being transported. This layer also checks if the data sent is correct or not.
FUNCTIONS:
SEGMENTATION: It is the process of dividing a data packet into smaller units over the network. It then reassembles at the destination.
FLOW CONTROL: It means sending the data to a rate that the receiver is capable of.
ERROR CONTROL: This keeps an eye on missing segments or duplicate segments.
PROTOCOLS USED:
TCP (Transport Control Protocol) provides data transfer without any loss that can be used for emails etc., UDP (User Datagram Protocol) provides data transfer with some loss possible that can be used for video calls etc.
5. NETWORK LAYER:
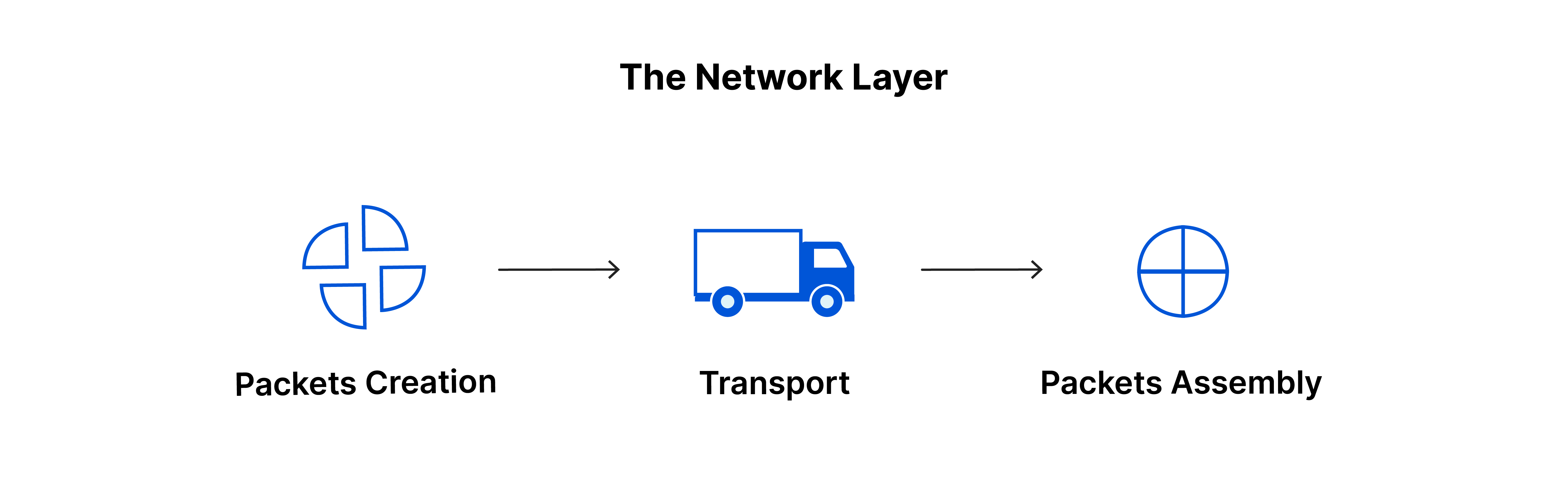
The transport layer passes data segments to the network layer. It is the layer where the router resides. This layer is responsible for the transfer of network packets from source to destination. It sets the best path for the data to travel.
FUNCTIONS:
LOGIC ADDRESSING: IP addressing done in the network layer is called logical addressing.
PATH DETERMINATION: Choosing the best possible path to transfer the data from one computer to another.
ROUTING: Routing is a method of moving data packets from source to destination. Based on the IP address format the data packet will first move to the network of the receiver and then into their system.
PROTOCOLS USED:
IP (Internet Protocol) address is a unique address that identifies a device a device on the Internet. It is a set of rules assigned to how data will be sent over the internet.
6. DATA LINK LAYER:
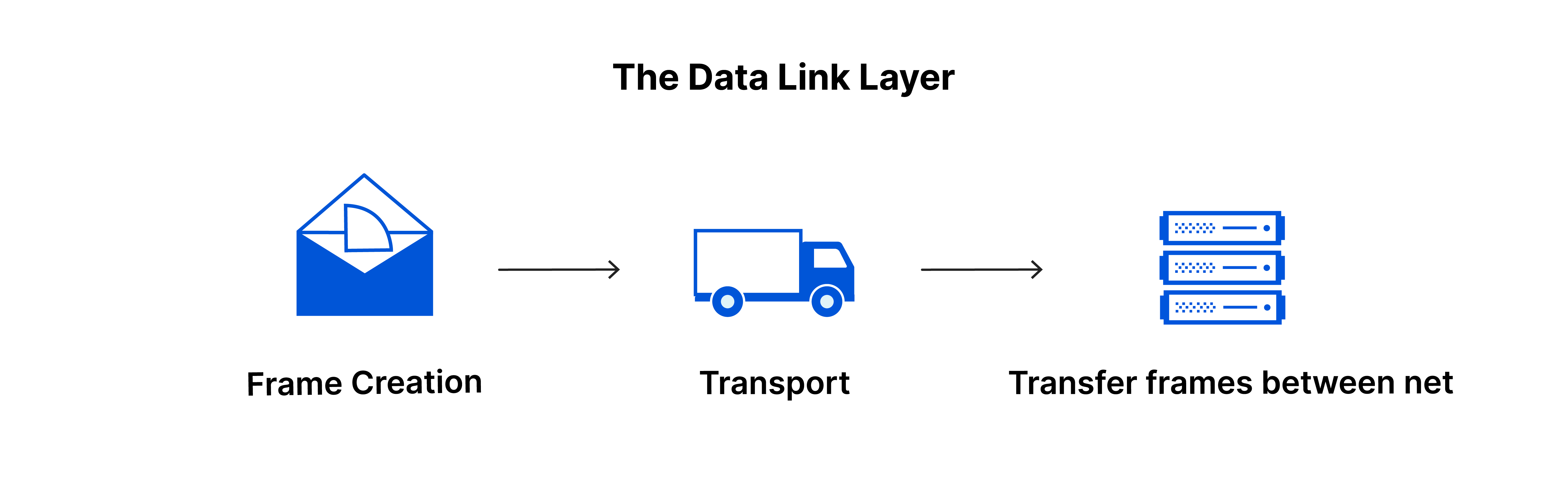
Data Link Layer takes the data packet from the network layer and breaks them into smaller pieces called frames. This layer is also responsible for flow and error control.
FUNCTIONS:
FRAMING: Packets received from the network layer are called framing. A received data packet will be sent to the physical layer bit by bit. It also takes frames from the physical layer and sends them to the network layer.
ADDRESSING: The data link layer encapsulates the source and destination’s MAC physical address in the header of each frame to ensure node-to-node delivery
ERROR AND FLOW CONTROL: Corrupted data,s correction is the responsibility of the data link layer. The data link layer also synchronizes the sender's and receiver's speeds.
PROTOCOLS USED:
NCP (Network Control Protocol ) is a set of protocols forming a part of Point-to-Point Protocol (PPP), LCP (Link Control Protocol) is a part of PPP that operates in the data link layer.
7. PHYSICAL LAYER:
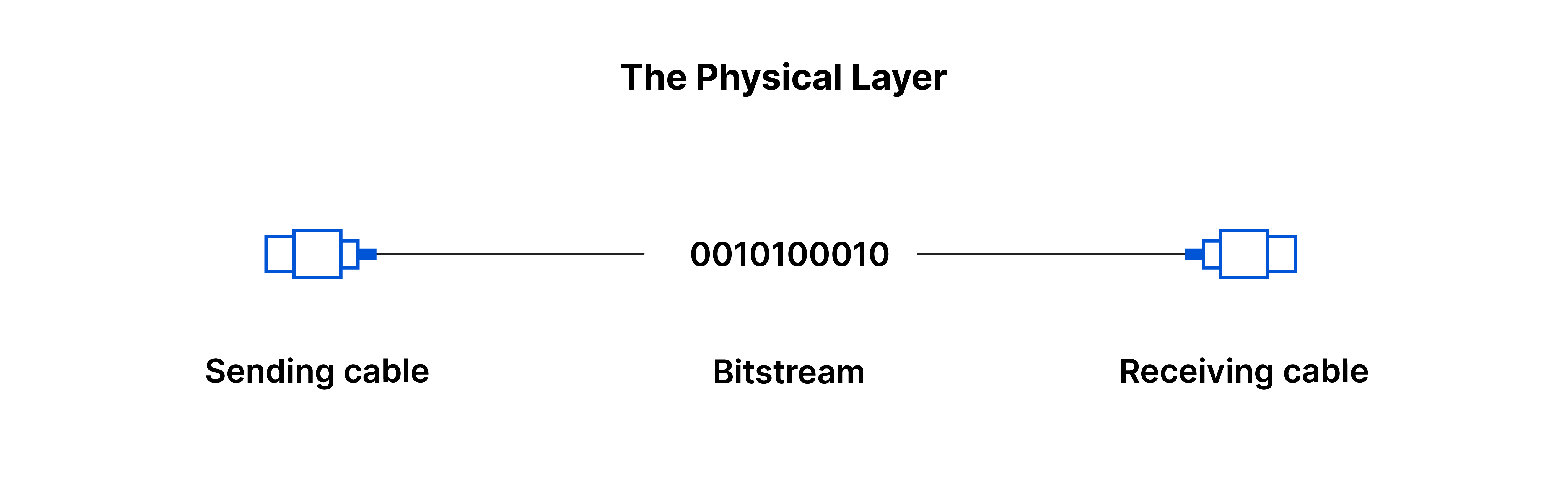
This layer includes physical components that are necessary from data transfer, like cables and switches. This is the layer where data gets converted into bit streams (basically it is a string of 1s and 0s).
FUNCTIONS:
physical layer is the only layer in the OSI model that deals with physical connectivity and is responsible for establishing, maintaining and deactivating the physical connections of two different computing devices in a network.
The physical layer controls the flow of data rate.
It also deals with bit synchronization discussed above.
Since we have discussed all 7 layers of the OSI model in detail, now it is time to jump on to some real-life examples.
REAL-WORLD EXAMPLE OF OSI MODEL:
EMAIL WORKING
Suppose you want an email to your friend. You open your browser and then the mail website from where you type your mail and tap on the send button. This mail then passes on to the application layer which will pick SMTP (used for emails) and pass the data to the presentation layer. The presentation layer will compress the data and then pass it to the session layer. In the session layer, the whole communication will start as it will start a session.
The data is then broken down into segments in the transport layer. Then those segments will be broken up into packets in the network layer, which will further be broken down into frames in the data link layer. The Data link layer then delivers those frames to the physical layer where they get converted into bit streams of 1s and 0s and sent through a physical medium such as cable.
Now, once your friend's system receives the bit stream through the physical layer (Wi-Fi etc.), the bit stream will flow through the same series but in the opposite direction.
The physical layer will convert the bit stream into frames and pass it to the data link layer. The data link layer then reassembles the frames converts them to packets and sends them to the network layer. Then the network layer will convert the packets to segments and the transport layer will reassemble the segments into data.
The data will then flow into the receiver's session layer, which will pass the data along to the presentation layer and then end the communication session. The presentation layer will then remove the compression and pass the raw data up to the application layer. The application layer will then feed the human-readable data along to your friend's email software, which will allow him to read your email on her laptop screen.
Thanks for reading !!


